The Encryption Cliff: Why Quantum Computing Changes Everything
For decades, the security of digital life—from secure bank transactions to military communications—has rested on the bedrock of Public Key Cryptography (PKC), specifically algorithms like RSA and Elliptic Curve Cryptography (ECC). These methods rely on mathematical problems that are currently too difficult for classical computers to solve within a reasonable timeframe.
However, the advent of fault-tolerant quantum computers threatens to shatter this foundation. A sufficiently powerful quantum machine, running Shor’s Algorithm, could break current standard encryption in a matter of hours, compromising data protected today that needs to remain secret for years (known as “Harvest Now, Decrypt Later” threats).
This isn’t a theoretical concern; it’s an existential security deadline. For IT professionals, CISOs, and business leaders (35-55), the question is not if the threat will materialize, but when. The solution is an urgent and non-negotiable transition to Post-Quantum Cryptography (PQC): new algorithms designed to withstand attacks from future quantum machines.

The Core Threat: Understanding the Quantum Leap in Decryption
The danger of quantum computing is rooted in the fundamental difference between how classical bits and quantum qubits operate.
Shor’s Algorithm and the PKC Breakdown
Classical computers perform calculations sequentially, while quantum computers leverage superposition and entanglement to explore multiple possibilities simultaneously. Shor’s algorithm, specifically designed for prime factorization and discrete logarithms (the basis of RSA and ECC), provides an exponential speedup.
-
Impact: A task that might take a classical supercomputer billions of years to complete could, theoretically, be completed by a large-scale quantum computer in hours or minutes.
-
The Window of Vulnerability: Any encrypted data traveling today, including corporate secrets, intellectual property, and personal records, is already at risk. Malicious actors are recording and storing this data now, anticipating the day a powerful quantum machine arrives to decrypt it en masse. This highlights the urgency of initiating NIST PQC Migration.
The Hybrid Approach: Mitigating Risk Today
Since the exact timeline for a catastrophic quantum attack remains uncertain, the industry consensus, led by organizations like the National Institute of Standards and Technology (NIST), is the Hybrid Cryptography approach.
This involves pairing existing, robust classical algorithms (like AES-256) with new, standardized PQC algorithms in a single communication channel. If either the classical or the quantum algorithm holds, the communication remains secure. This strategy offers immediate protection and serves as a vital bridge during the multi-year migration process.
The Solution: NIST and the PQC Migration Roadmap
The foundation of the Post-Quantum Cryptography solution rests on replacing the vulnerable math problems of RSA/ECC with new, hard-to-solve problems that even quantum computers cannot crack efficiently.
Key PQC Families
NIST has selected four primary families of PQC candidates, each relying on different mathematical foundations:
-
Lattice-based Cryptography (Kyber/Dilithium): Currently the leading choice, this relies on the complexity of solving specific shortest-vector problems in multi-dimensional lattices. It is favored for its speed and relative simplicity.
-
Code-based Cryptography (Classic McEliece): Uses error-correcting codes. Known for high security but often requires larger key sizes.
-
Hash-based Signatures (SPHINCS+/Leighton): Highly efficient for digital signatures and authentication.
Strategic PQC Migration Phases
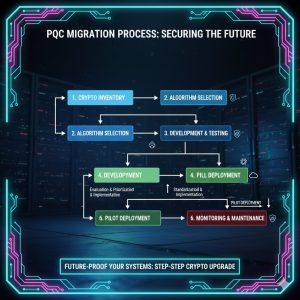
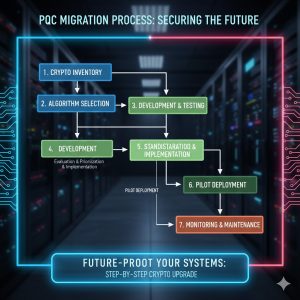
A successful PQC Migration for an enterprise network is not a single upgrade, but a multi-phased strategy.
-
Phase 1: Inventory and Discovery (The ‘Crypto-Agility’ Audit): Identify every piece of hardware, software, and protocol (VPNs, TLS/SSL, digital signatures) that utilizes public-key cryptography. This is the most complex phase, requiring a deep audit of legacy systems and embedded firmware.
-
Phase 2: Standardization and Testing: Implement the new hybrid algorithms (using NIST-selected standards like Kyber) in non-critical environments. Begin testing for performance overhead, as some PQC algorithms can be more computationally intensive than their classical counterparts.
-
Phase 3: Deployment and Decommissioning: Deploy the PQC-enabled systems and formally decommission the old RSA/ECC keys. NIST PQC Migration is expected to be a multi-year effort spanning the entire decade.
Business Imperative: Data Security vs. Migration Complexity
The biggest hurdle in the PQC Migration is not the math, but the practical IT complexity. The sheer number of systems and devices that require updates presents a massive logistical challenge.
Hardware and Firmware Limitations
Many embedded systems, IoT devices, and older firewalls have limited memory or processing power. They may be unable to handle the larger key sizes or the computational load required by some PQC algorithms, necessitating costly hardware replacement rather than just a software update. This is especially true for devices whose firmware cannot be updated by vendors who are no longer supporting the product.
The Cost of Inaction
The cost of delaying the PQC transition far outweighs the migration budget. Organizations in healthcare, finance, defense, and intellectual property-driven industries must prioritize PQC migration immediately. A failure to act will expose them to the inevitable Quantum Threat Data Security breaches of the future.
Successfully navigating this transition requires prioritizing cryptographic agility—the ability to rapidly switch or update cryptographic algorithms without significant downtime. This architecture must be built into all new product deployments today.
REALUSESCORE.COM Analysis Scores: PQC Readiness
This analysis evaluates the perceived urgency and complexity facing businesses regarding the shift to Post-Quantum Cryptography (PQC).
| Analysis Feature | Urgency (1-10) | Complexity (1-10) | Analysis Explanation |
| Quantum Threat Data Security Risk | 9.5 | 6.0 | High urgency due to “Harvest Now, Decrypt Later” threat. Low complexity of understanding the risk. |
| NIST PQC Migration Logistical Scale | 7.0 | 9.5 | Requires comprehensive inventory across all hardware/software; a massive logistical undertaking. |
| Cost of Inaction (Future Breach) | 10.0 | 1.0 | A successful quantum breach means total data compromise; the cost is maximal. |
| Cryptographic Agility Investment | 8.5 | 7.5 | Investment in rapid algorithm switching is vital; high cost but necessary for future resilience. |
Conclusion: Act Now, Before the Quantum Leap
The transition to Post-Quantum Cryptography is the most significant cryptographic shift in decades. It demands a phased, intentional strategy starting with a comprehensive inventory audit. Delaying action will only compound the technical debt. By embracing the NIST standards and prioritizing cryptographic agility, businesses can ensure that their valuable data remains secure against the inevitable arrival of the quantum age, effectively neutralizing the Quantum Threat Data Security risk.

