The age of quantum computing is dawning. Post-Quantum Cryptography Explained is not merely a theoretical concept. Instead, it is an urgent requirement for global digital security. Many experts now predict that a powerful quantum computer—one capable of breaking today’s encryption—could arrive within a decade. Therefore, the cryptographic community is moving quickly. They are urgently transitioning toward quantum-resistant algorithms.
1. The Looming Quantum Threat: Shor’s Algorithm
Current internet security, which encompasses TLS, VPNs, and e-commerce, relies heavily on public-key systems. These include RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography). The security of RSA, for example, is based on one difficult problem: the computational infeasibility of factoring very large numbers. Crucially, a classic computer would take longer than the age of the universe to factor a 2048-bit RSA key.
However, this foundational security assumption crumbles in a quantum world. Shor’s Algorithm, developed by Peter Shor in 1994, is a quantum algorithm. It can solve the integer factorization problem exponentially faster than any classical method. Consequently, the algorithm leverages quantum parallelism and interference. It can find the prime factors of a public key in a feasible amount of time. In essence, a sufficiently powerful quantum computer running Shor’s Algorithm could render RSA and ECC obsolete. This would expose previously secure communications to decryption.

2. The PQC Solution: Lattice-Based Cryptography
In response to this looming threat, the field of Post-Quantum Cryptography (PQC) has rapidly emerged. PQC aims to develop algorithms that remain secure against both classical and quantum attacks.
The clear front-runner in this domain is Lattice-Based Cryptography (LBC). A lattice is a geometric structure, essentially a regular, grid-like arrangement of points in multi-dimensional space. Specifically, LBC’s security relies on the complex mathematical difficulty of solving “lattice problems.” These include the Shortest Vector Problem (SVP) and Learning With Errors (LWE). Moreover, these problems are believed to remain hard even for powerful quantum computers.
Furthermore, lattice-based schemes like CRYSTALS-Kyber (for key exchange) and CRYSTALS-Dilithium (for digital signatures) are highly efficient and versatile. These two algorithms form the core foundation of NIST’s final selections for PQC standards.
(For related technical analysis, check out our previous discussion on Tech Review: PQC Adoption Strategy.)

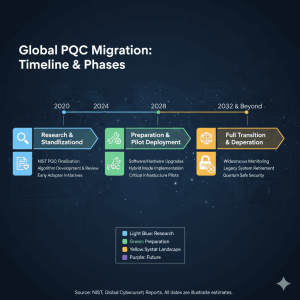
3. NIST’s Critical PQC Transition Timeline
The transition is now gaining momentum, largely guided by the U.S. National Institute of Standards and Technology (NIST). NIST has established firm deadlines to manage this unprecedented global shift. To illustrate, NIST published the first three finalized PQC standards (FIPS 203, 204, 205) in August 2024.
The official timeline holds critical importance for all organizations:
- By 2030 (Deprecation): Quantum-vulnerable algorithms, such as RSA-2048 and ECC-256, will be officially deprecated. Organizations must transition to PQC algorithms by this deadline.
- After 2035 (Disallowed): These vulnerable algorithms will be completely disallowed from use in secure communication systems.
Therefore, 2035 must be seen as a hard deadline, not a starting point. Organizations must begin auditing their cryptographic systems and developing hybrid migration strategies immediately.
(You can track the official standardization progress directly on the NIST Computer Security Resource Center website.)
4. What You Can Do Now
This challenging transition requires proactive and strategic planning. For example, systems handling long-term confidential data (e.g., VPNs, TLS, PKI) should be prioritized for migration first.
Ultimately, a smooth transition hinges on cryptographic agility—the ability to easily swap out algorithms as new standards and updates emerge. For related insights on adapting to new technology, read our review of evolving data security in the Product Review: Best OLED TVs of 2025.)
The quantum threat is no longer distant. The time to understand Post-Quantum Cryptography Explained and implement the new lattice-based algorithms is now.